It has been a while since I posted anything on my blog, but following a very busy couple of months I’ve decided to do a quick piece on the dangers of downloading legacy installation files from filesharing sites, as well as praise some of the great customer service I received from one company in particular, whilst I was doing some research for a case.
To many the advice I’m going to offer should be very obvious, but to some this might be valuable nuggets of information that may well save your systems and data from disaster. Either way, I hope it makes for a fun and interesting read.
The Case
So the last few weeks I’ve been working on some devices where the user frequently installs and uses the well known software program, CCleaner (by Piriform), on their windows systems. They have several devices, and each one has a different version of CCleaner installed (typical!). The details behind the case are not something I will disclose, but in short, I wanted to know a little bit more about how CCleaner works, stores logs and whether there are variations in default settings, or the way configurations are stored and monitored by the program across different versions.
CCleaner comes in both free and paid versions, with the usual model of free (limited ‘lite’ versions for home users) and paid for pro versions (functionality fuelled for business and the security conscious).

My subject was using the free versions, which made life a little easier for me purely from the ability to gain access to the installation files and run tests across the different versions.
My plan was to generate a virtual machine (VM) of the same host operating system to test the various versions on (in this case I needed two VMs: Windows 7 Home Edition, and Windows 10 Home as upgraded from Windows 7 Home Edition) and install in-turn each of the different versions of CCleaner, identify the default settings and setup, pull the configuration files, hash them and compare these all against the settings and configuration files I had on the devices I was examining. A simple but effective test for a quick comparison. There are more in-depth and scientific ways to do this, but time is a luxury that I did not have.
Obtaining the Legacy Installer Files – The Risky Method
Unfortunately for me, Piriform only have the latest version of CCleaner available to download from their website, and the versions I needed dated back to around 2010/11, and so I needed to find an alternative method of obtaining the files.
Out of curiosity I searched the web for the relevant CCleaner version and two sites immediately came to the fore, one I knew well and the other…not so much.
The site I knew well, and is likely known by many of you, was FileHippo (Image 2) and the not so well known site was ‘Brothersoft‘ (Image 3).
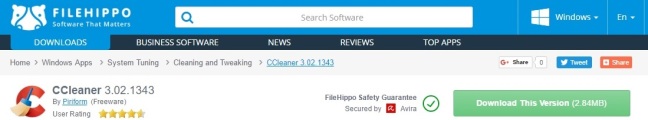
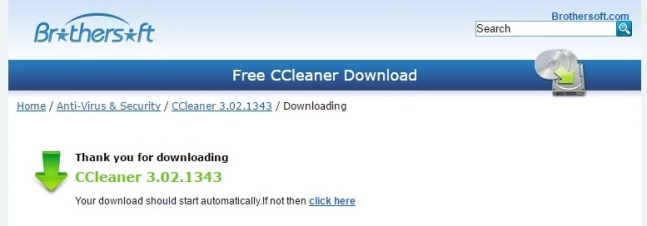
Image 3: Screenshot from Brothersoft (Brothersoft.com)
Both sites claimed to have the version of CCleaner v.3.02.1343 available for download, and both claimed to be safe and secure. I am always suspicious of such things, and whilst I had another method in mind to obtain the files (which I will explain shortly), I decided to fire up another locked down VM, remove access to my host machine from within it the best I could, secured my browser by forbidding various scripts and autorun features, and downloaded the files (albeit, not open or run them).
The FileHippo file came down with the traditional filename format for CCleaner of ccsetupXXX.exe (with the XXX being the version number), whereas the Brothersoft file actually appeared with a different name, “Installer_for_CCleaner.exe” (how very interesting!). As you can imagine, alarm bells were already ringing on this one.
At this point I didn’t have a confirmed original hash value of the genuine installer file in question, and so I was unable to verify whether either file was what it claimed to be, so I decided to run both files through VirusTotal (www.virustotal.com) which is a cracking site for checking files and URLs for malware and nasty surprises.
I uploaded both files, firstly the brothersoft download (Image 4) and secondly the FileHippo download (Image 5) with the following results:
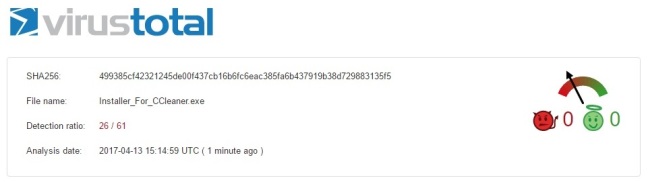
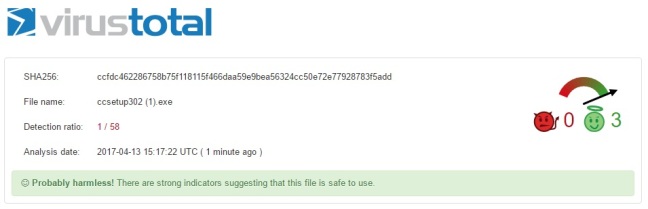
As you can see, despite both files claiming to be the genuine article, both vary greatly in their scan results, with the FileHippo file potentially being the genuine installer, whilst the Brothersoft download is clearly not as it should be!
Another sign was the file sizes – CCleaner installer files have grown in size from one version to the next, with the latest version to date (v5.28) sitting at around the 9MB mark, whilst the version I was after here was around the 3MB mark. The Brothersoft installer file registered a file size of less than 1MB, which was suspicious in itself, with my immediate thoughts being that this was a simple payload dropper of sorts which will call out to a command and control server (C2) to malicious download and install some nasty malware if the program was run. Definite sad face moment!
Obtaining the Legacy Installer Files – The Safer Method
So the method I was always going to use was to contact Piriform directly and ask them whether I could have access to their legacy installers for the specific versions in question for my forensic analysis.
Now I have to say that Piriform were absolutely fantastic! I cannot fault them for their customer service and have passed on my thanks to them for their support. They responded to my request within a day (which included details on log files and configurations etc as well) with copies of the original installer files, hash values, and gave me the command line run options to generate the .INI configuration files and make them accessible on my system for the default settings associated to that version of the software.
For reference, I was given the below advice:
If you need to review the complete list of default/non-default cleaning definitions that are available in these versions of the product, you can extract the winsys and winapp INI files from them as follows:
- Open the “Run” dialog in Windows (Windows Key +R)
- Type exe /EXPORT > click OK
After this, the INI files will appear in C:\Program Files\CCleaner, or in whichever folder location the software was installed at.
This worked a treat! It wasn’t available for the v3.02.1343, but the later versions I requested this worked wonderfully and is something worth noting if you ever need access to these files in the future!
What is also handy to note regarding these files is the following:
…currently, we only have the default settings (in terms of cleaning options) available for review in the format of our program’s INI files, and I’ve attached these to this email for you.
(see attached “winsys.ini” and “winapp.ini” files)
If a default setting, the INI file will show “Default=True” whereas if a non-default setting, the INI file will show “Default=False”.
If you have any questions about this, or if you need anything, please let me know – I’ll be glad to help.
Out of curiosity I ran the installer file v3.02.1343 though virustotal and compared the hash and discovered that the FileHippo file was the genuine article (huzzah!) and clearly the dodgy Brothersoft download was malicious and full of nasty malware!
In conclusion…
So to finish, whilst this wasn’t the most scientific research process, I wanted to highlight this to anyone who may be interested for several reasons:
- Be careful where you download files from and never ever run them without confirming they are genuine.
- Never be afraid to contact the developers, suppliers or manufacturers to obtain legacy software if you are in need of it. They will most likely oblige wherever possible and give you some level of support.
- Piriform are awesome! 🙂
I hope you’ve found this useful or interesting, and please don’t hesitate to contact me if you want to know more (obviously, I won’t be disclosing any details about cases…this blog is merely to help provide security advice and tips for forensic analysts)

